Description of Cryptowall 2.0
Cryptowall
2.0 is classified as ransomware which is
capable of encrypting your personal date and files stored on your computers. It is the newest version of the Cryptowall. Broadly
speaking, this malware often sneaks into the target computer via being
bundled with free downloads, visiting intrusive websites, downloading spam
email attachments, opening malicious links, or clicking suspicious links.
While being infected, this ransomware will firstly store itself in
the Temp folder as a random named executable. At the same time, it will
create a hidden random named job in Task Scheduler so that this malware
launches executable every time you start up your computer. Thus this malware
will be able to scan your computer for important personal files and encrypt
them so that you can
no longer open them.
Meanwhile, this ransomware will rename your files so that they end
with a Cryptowall extension. So these files are simply your normal data
files that have been encrypted. If you attempt to open a file with a program,
the program may state that it is corrupted or just display garbled text on the
screen. The only way to recover these files so that they show the original, and
correct, information is to restore them in some manner or pay the ransom.
Moreover,
this malware can hijack all your most used web browsers and redirects you to some
irrelevant websites. And millions of unwanted ads show up tricking you to click
to bring more infections into your computer.
Furthermore,
this malware always looks for security vulnerabilities to bring other viruses
into your computer to make further damage to your computer. In addition, your computer
will take a long time to turn on or shut down after being attacked by this rogueware
and even get the blue or black screen of death which can further damage your
computer hardware.
In a
word, the Cryptowall 2.0 is a ransomware which is able to bring many troubles
to your computer security and your own privacy. Therefore, you should take
prompt actions to get rid of Cryptowall 2.0 from your computer once it is found
before it does more damages.
Symptoms of Cryptowall 2.0
- Your personal files have been encrypted without your execution and you cannot open it.
- A ransom screen that states your files were encrypted and prompts you to follow the instructions on the screen to pay the ransom for your files shows up.
Damages of Cryptowall 2.0
- It can scan and encrypt your files so they are no longer accessible.
- It violates your right for knowledge and property safety.
- It can hijack your browsers.
- It can mess up your computer via downloading more malware and other infections and finally crash the computer itself down.
Removal Guide for Cryptowall 2.0
A. Get Rid of Cryptowall 2.0 Manually
To manually remove the infection you should remove any executable from the Temp folder and then clean the hidden job in the Windows Task Scheduler.
Step 1: Remove any executable from the Temp folder.
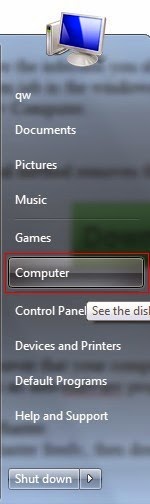
1) Click Start > Computer.
Step 2: Clean the hidden job in the windows Task Scheduler.
1) Click on Start and type in "Task Scheduler" to search it.
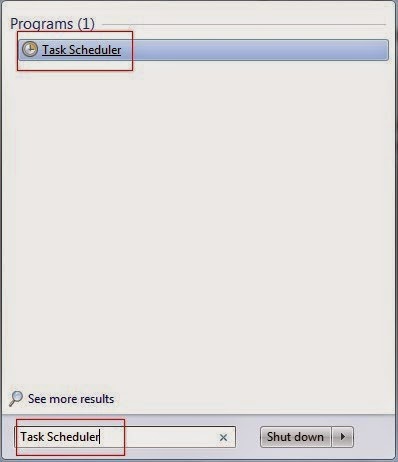
2) After the Task Scheduler window shown, find out and clean the hidden job.
Notice: The removal method removes the main infection, but will not restore your encrypted files.
B. Get rid of Cryptowall 2.0 Automatically with SpyHunter
As soon as you discover that your computer is infected with Cryptowall 2.0, you should fully scan your computer and fix the threats automatically with an anti-malware program. Here makes SpyHunter as an example.
Step 1: Install SpyHunter.
1) Download SpyHunter here.
Step 2: Fix all the detected threats with SpyHunter.
1) Open SpyHunter and click on Scan Computer Now! to start a full scan on your computer.
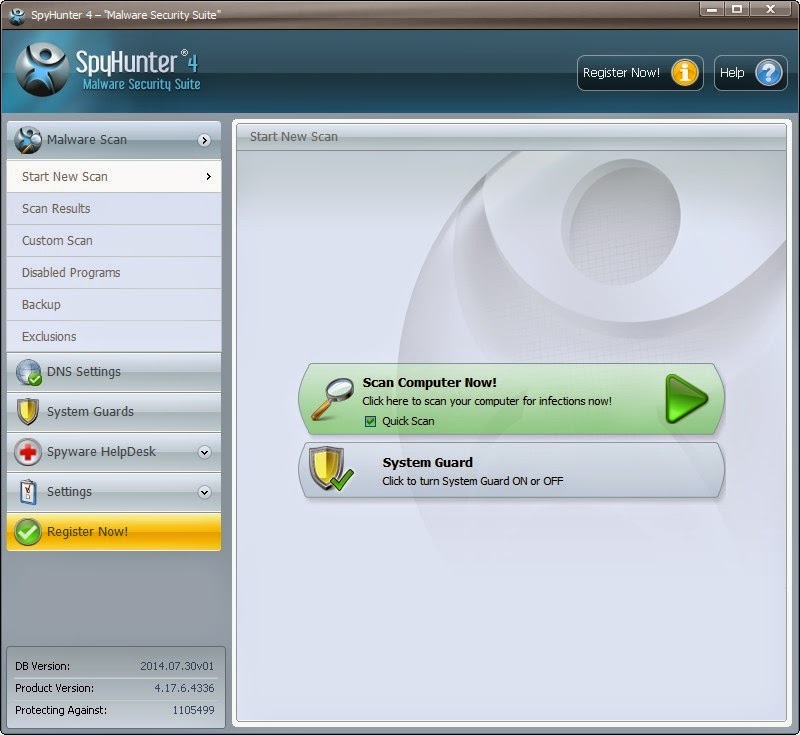
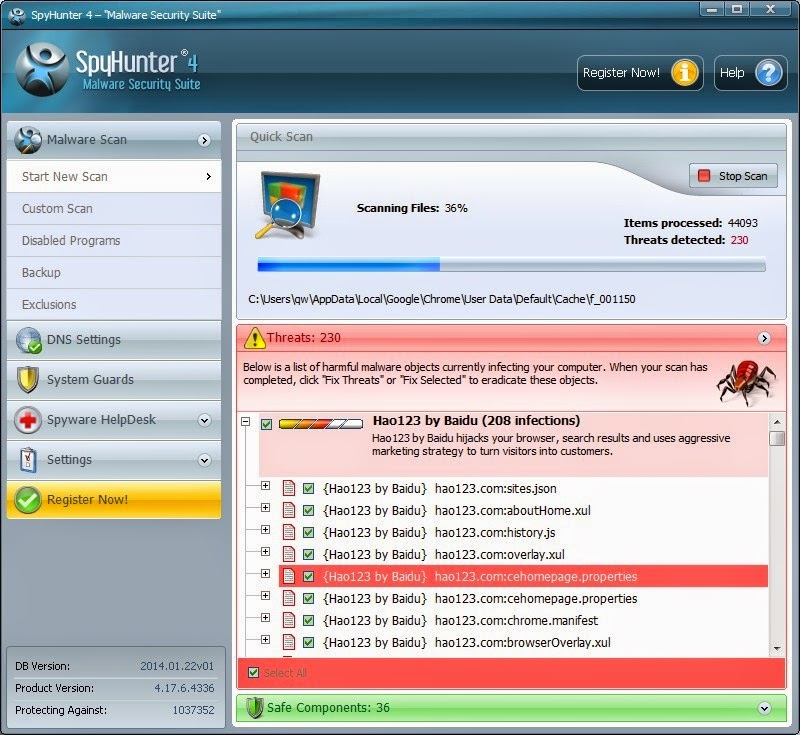
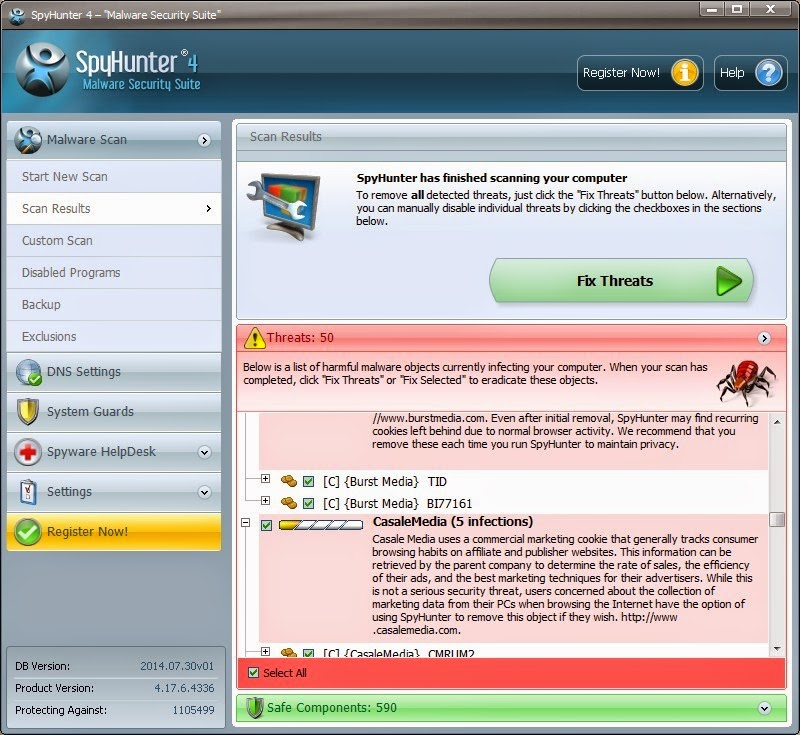
Notice: It is recommended to apply the later solution to get rid of Cryptowall 2.0 with SpyHunter. The scan will detect and remove the infections from your computer so that it no longer starts when you login to Windows.
C. Uninstall Unwanted Programs Downloaded by Cryptowall 2.0 Automatically with Perfect Uninstaller
Step 1. Download Perfect Uninstaller here, and then install the program step by step.
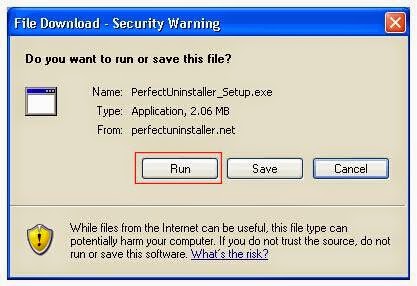
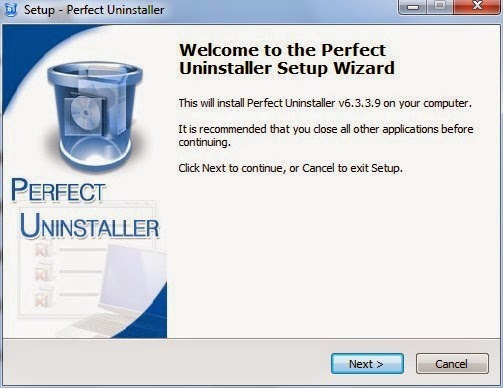
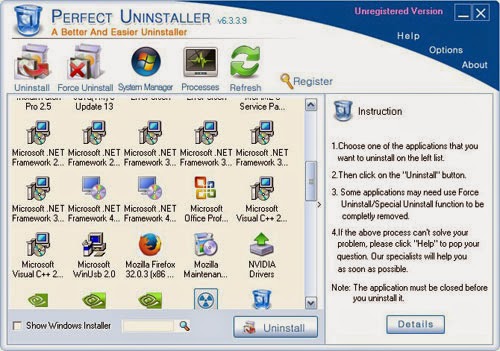

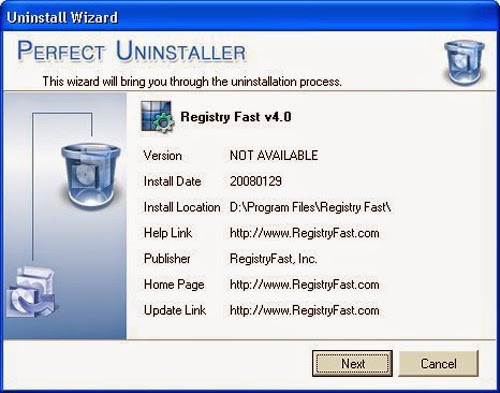

Notice: If SpyHunter cannot completely remove the programs and files associated with Cryptowall 2.0, you can use Perfect Uninstaller to help you deal with them. Perfect Uninstaller is an advanced and effective tool which is able to safely completely uninstall any unwanted or corrupt application that other anti-malware program cannot remove, and it also can help you manage your startup items and backup system so that to speed up your computer performance. You can download Perfect Uninstaller here and it will help you uninstall all the unwanted programs in your computer effectively and permanently.

No comments:
Post a Comment